- Course
Volt Typhoon: T1070.003 Indicator Removal Emulation
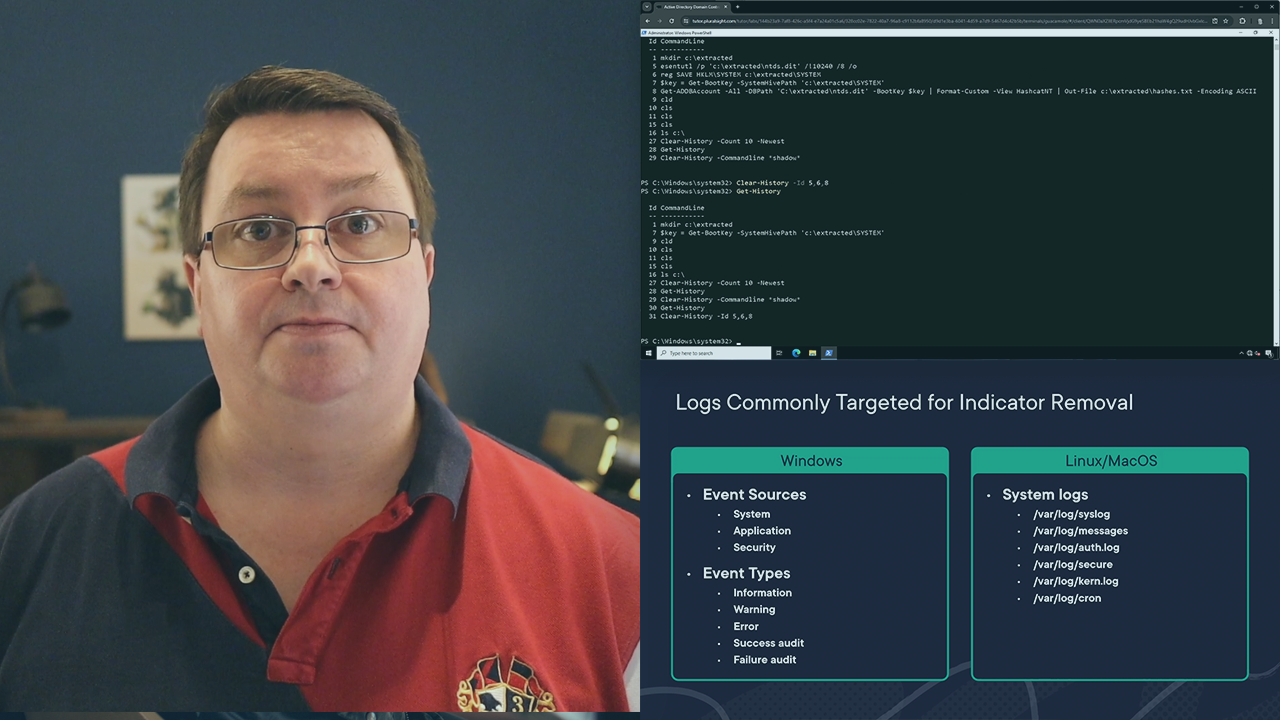
Explore how and why Volt Typhoon removed or modified files left behind by the actions of their intrusion activity in critical infrastructure networks.
- Course
Volt Typhoon: T1070.003 Indicator Removal Emulation
Explore how and why Volt Typhoon removed or modified files left behind by the actions of their intrusion activity in critical infrastructure networks.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
Non-native files such as tools and malware used during an attack may leave traces to indicate what was done by an adversary and how they did it. A common technique used by adversaries to hide their tracks is to remove these files either during an intrusion, or as part of post-intrusion activities. In this course, Volt Typhoon: T1070.003 Indicator Removal Emulation, explore how the Volt Typhoon threat group used this technique to minimize their footprint on systems and remain undetected in critical infrastructure for over 5 years.

