- Course
Windows Identity Foundation Patterns: On-Premise and Cloud
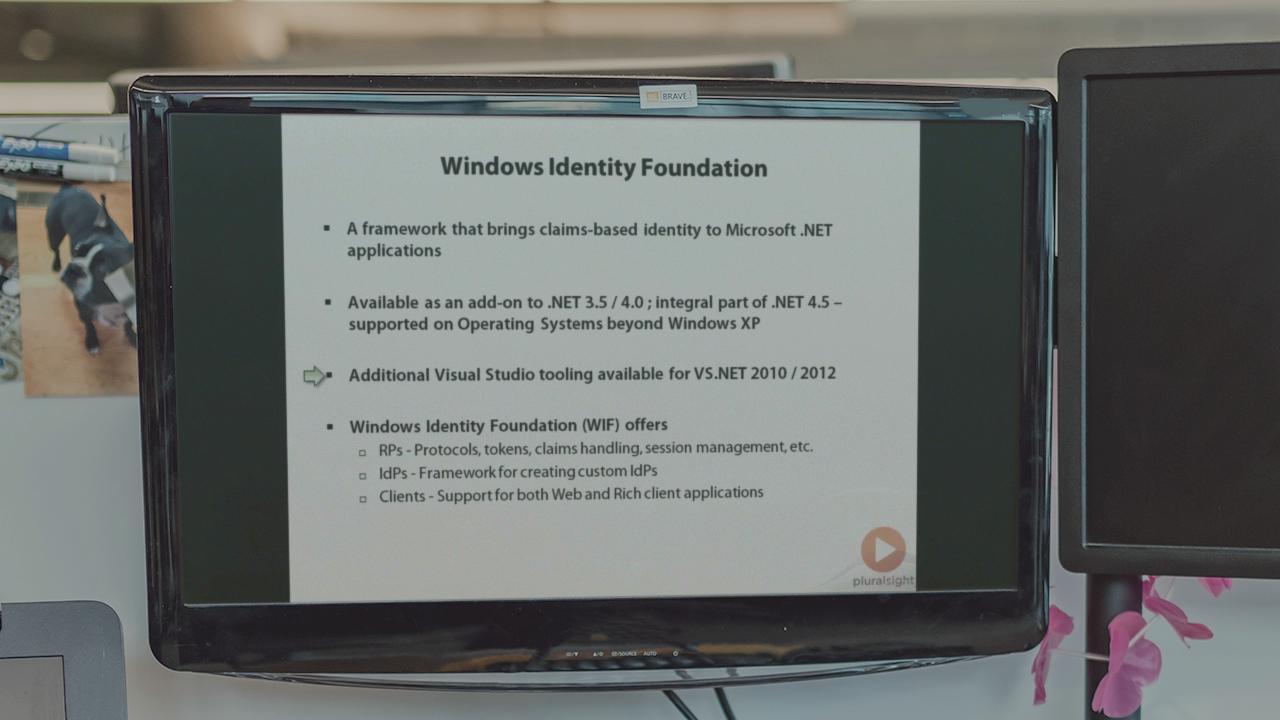
This course aims to demystify on-premise and cloud-based identity solutions.
- Course
Windows Identity Foundation Patterns: On-Premise and Cloud
This course aims to demystify on-premise and cloud-based identity solutions.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Core Tech
What you'll learn
Dealing with multiple identities has always been challenging; even more so with the advent of the cloud. Developers and architects are often confused by the numerous terms, acronyms and buzzwords - such as Active/Passive Federation, SWT, SAML, ADFS, WIF, WS-Trust, WS-Federation, OAuth, OAuth WRAP and others. This course starts by distilling the technology jargon; setting the foundation for understanding various identity solutions. Having laid the foundation, this course then focuses on typical claims-based identity solution patterns within enterprises. Understanding these recurring implementation themes will further simply the mapping of claims-based identity to your LOB applications.

