- Course
Zero Trust Architecture (ZTA): Use Case Identification and Implementation
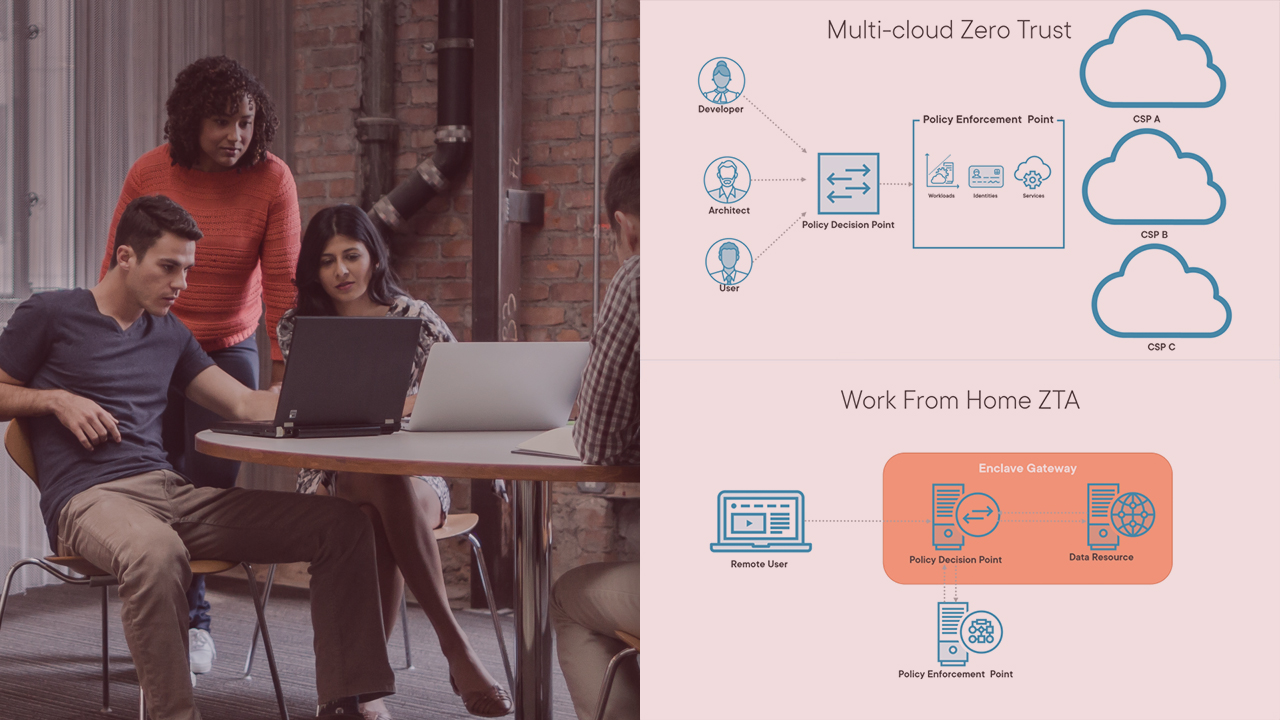
Zero trust architecture provides the basis for greater security assurance. This course will teach you to identify, develop, and implement use cases for zero trust architecture.
- Course
Zero Trust Architecture (ZTA): Use Case Identification and Implementation
Zero trust architecture provides the basis for greater security assurance. This course will teach you to identify, develop, and implement use cases for zero trust architecture.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
Zero trust architecture provides the basis for greater security assurance. In this course, Zero Trust Architecture (ZTA) Use Cases, you’ll learn applicable use cases for implementing zero trust. First, you’ll explore use cases tied to multiple systems and services. Next, you’ll discover use cases connected to various user types. Finally, you’ll learn how to identify your unique use cases and prototype zero trust architecture implementation. When you’re finished with this course, you’ll have the skills and knowledge of use case identification and execution needed to establish your zero trust architecture.

