- Course
Defense Evasion with ProxyChains
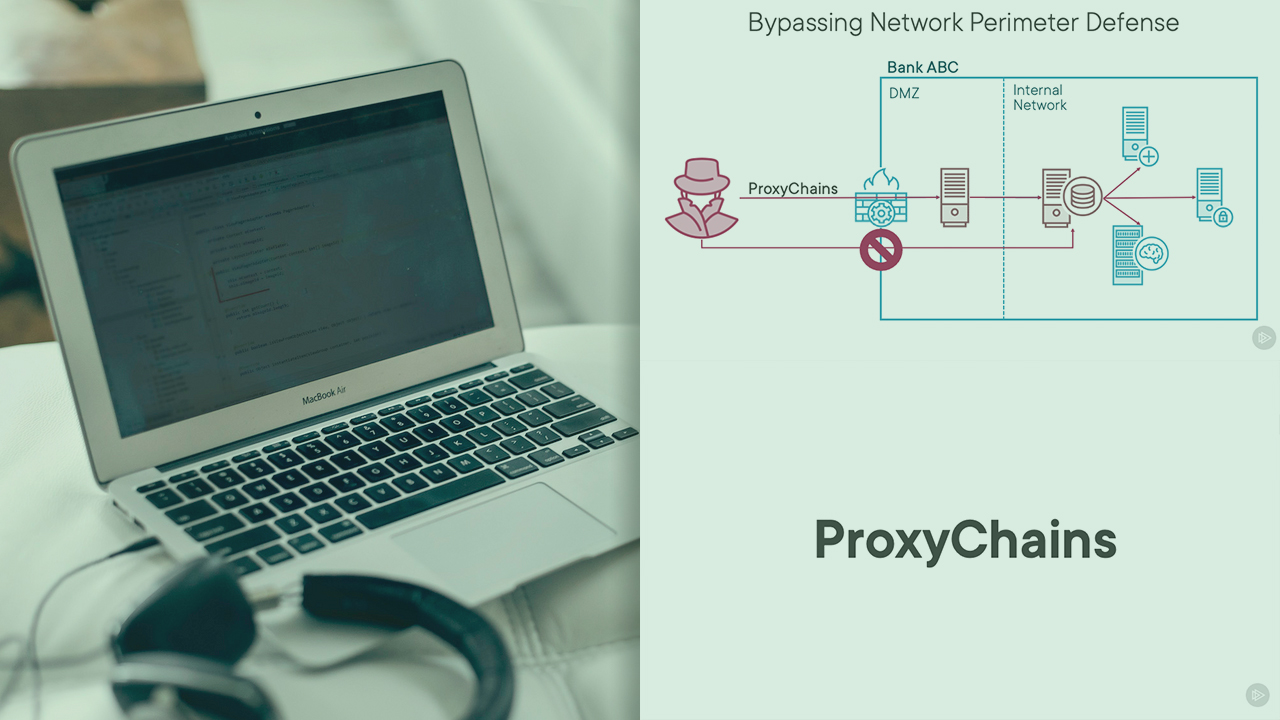
Network security tools are the most common line of defense in a company. In this course, you will learn how to use ProxyChains to re-route your network traffic and bypass such security tools.
- Course
Defense Evasion with ProxyChains
Network security tools are the most common line of defense in a company. In this course, you will learn how to use ProxyChains to re-route your network traffic and bypass such security tools.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
Virtually every company has a at least a firewall solution to prevent hackers from accessing internal servers. As a red team specialist, you job is to simulate a real attack and try to bypass such defense mechanisms. In this course, Defense Evasion with ProxyChains, you will learn how to bypass network defense tools by tunneling the traffic through compromised machines. First, you will explore what network defense evasion is and how ProxyChains can help you to accomplish that. Then, you will see how to obfuscate your real IP address by using ProxyChains and the TOR network. Finally, you will learn how to bypass network segmentation and firewall solutions by using ProxyChains to re-route your traffic through an already compromised machine. This course covers a tactic from the MITRE ATT&CK framework: Network Boundary Bridging (T1599).

