- Course
Detecting Anomalies and Events with Logstash
Logstash is a powerful tool for processing and analyzing log data. In this course, you will learn the setup, configuration, and validation of Logstash in an enterprise environment.
- Course
Detecting Anomalies and Events with Logstash
Logstash is a powerful tool for processing and analyzing log data. In this course, you will learn the setup, configuration, and validation of Logstash in an enterprise environment.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
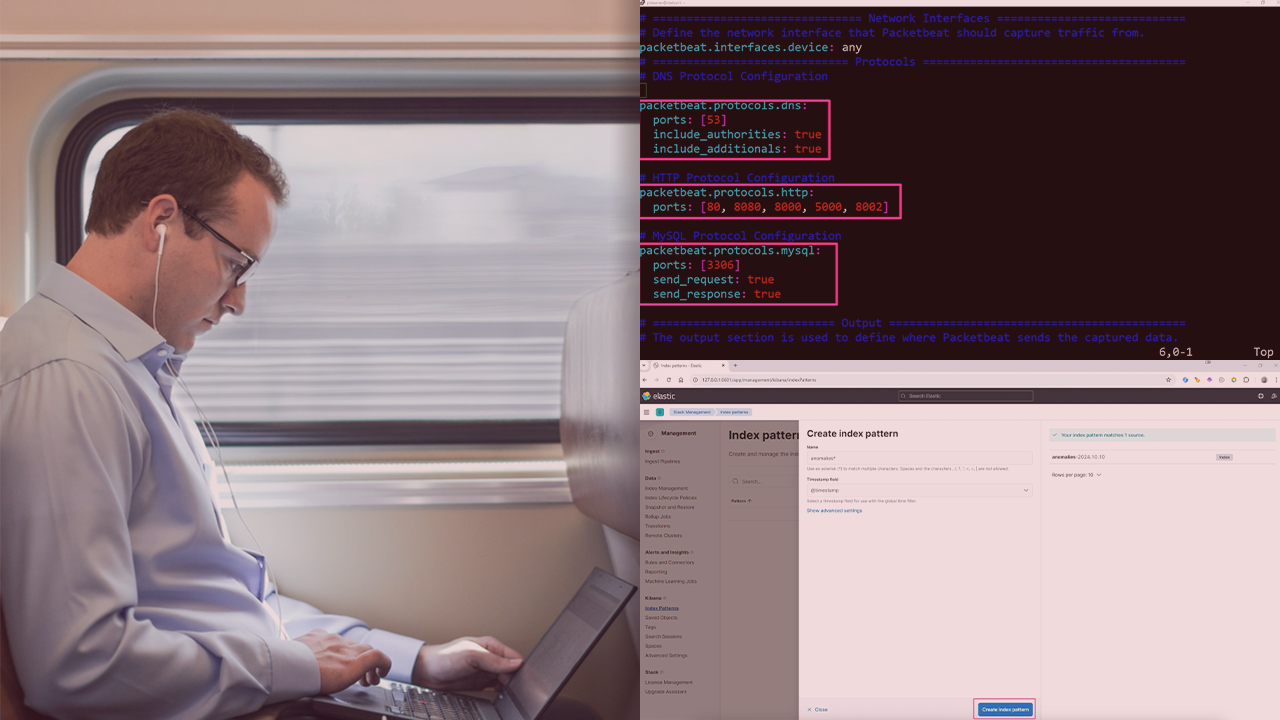
Enterprises often struggle with effectively monitoring and detecting anomalies in their network traffic, leaving them vulnerable to potential security breaches. In this course, Detecting Anomalies and Events with Logstash, you'll learn how to utilize Logstash to secure a live enterprise environment. First, you'll discover how to set up Logstash to ingest and process network traffic data. Next, you'll apply custom filtering rules to detect anomalies in DNS, HTTP, and MySQL traffic. Finally, you'll simulate real-world traffic to test Logstash's ability to detect and flag threats. When you're finished with this course, you'll have the skills and knowledge to identify, protect, detect, and respond to threats in your network systems.

