- Course
Leverage PowerShell Tools for Pen Testing
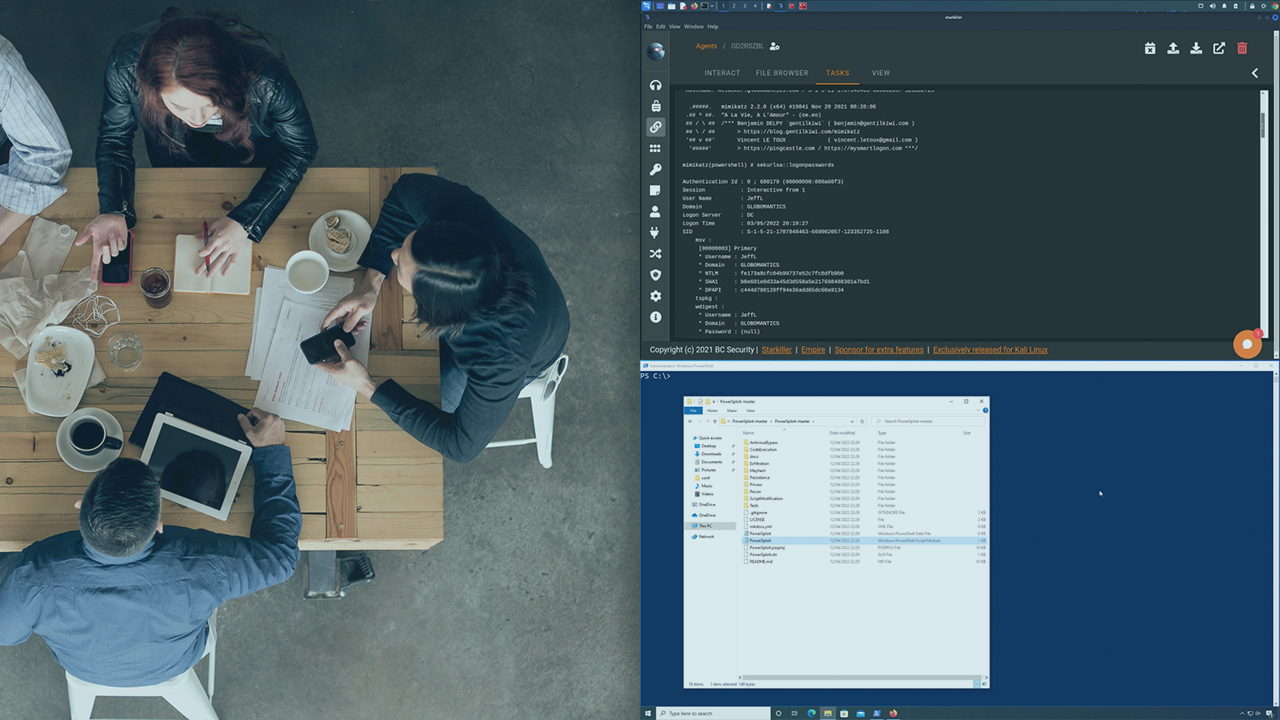
This course will teach you to leverage one of the most powerful built-in tools, PowerShell, for penetration testing.
- Course
Leverage PowerShell Tools for Pen Testing
This course will teach you to leverage one of the most powerful built-in tools, PowerShell, for penetration testing.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
Penetration testing is an essential task to ensure up-to-date security for your business. In this course, Leverage PowerShell Tools for Pen Testing, you’ll learn to effectively leverage PowerShell tools during a penetration test. First, you’ll explore situational awareness involving recon on a target environment. Here you will explore ways that you can execute PowerShell commands in memory and some of the tools from PowerSploit. Next, you’ll discover how to use the modules of Empire to further expand your grasp into the target network. Finally, you’ll learn how to work with PowerUpSQL to leverage PowerShell to obtain data from a SQL database. As an added bonus, you will cover some extremely useful tools to create PowerShell download cradles and obfuscate your PowerShell commands. When you’re finished with this course, you’ll have the skills and knowledge of leveraging PowerShell tools to enhance your pentesting skills.
Leverage PowerShell Tools for Pen Testing
-
Module Introduction | 35s
-
Defining Your Target Environment | 1m 37s
-
Traditional Way of Enumeration | 4m 52s
-
Enumeration with PowerView | 7m 34s
-
Enumerating Even More with PowerView | 5m 7s
-
A Little More Enumeration Won't Hurt! | 3m 37s
-
Using PowerUp to Escalate Privileges | 5m 22s
-
PowerShell Memory Execution | 7m 19s
-
Module Summary | 53s

