- Course
Network Security Testing With NMAP
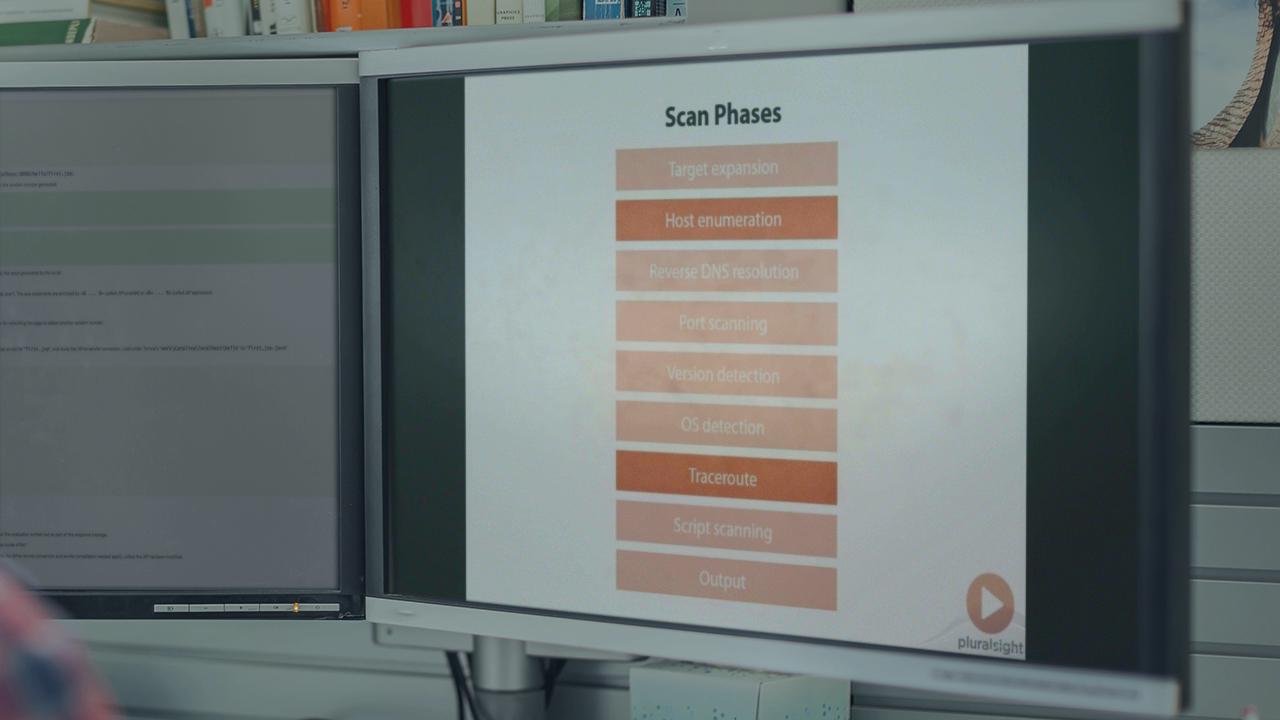
This course presents NMAP, a network scanning tool, from basic usage through advanced service analysis.
- Course
Network Security Testing With NMAP
This course presents NMAP, a network scanning tool, from basic usage through advanced service analysis.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
NMAP is a powerful network scanning tool that can be used by a network administrator or security practitioner to audit a network. This course will lead the student through a discussion of NMAP's scanning phases and a discussion of the tool's capabilities and options for network, host, and service discovery. After completion of the course, the student will have a thorough knowledge of NMAP and be able to use it to effectively ensure the security of their network.

