- Course
Effective OAuth2 with Spring Security 5 and Spring Boot
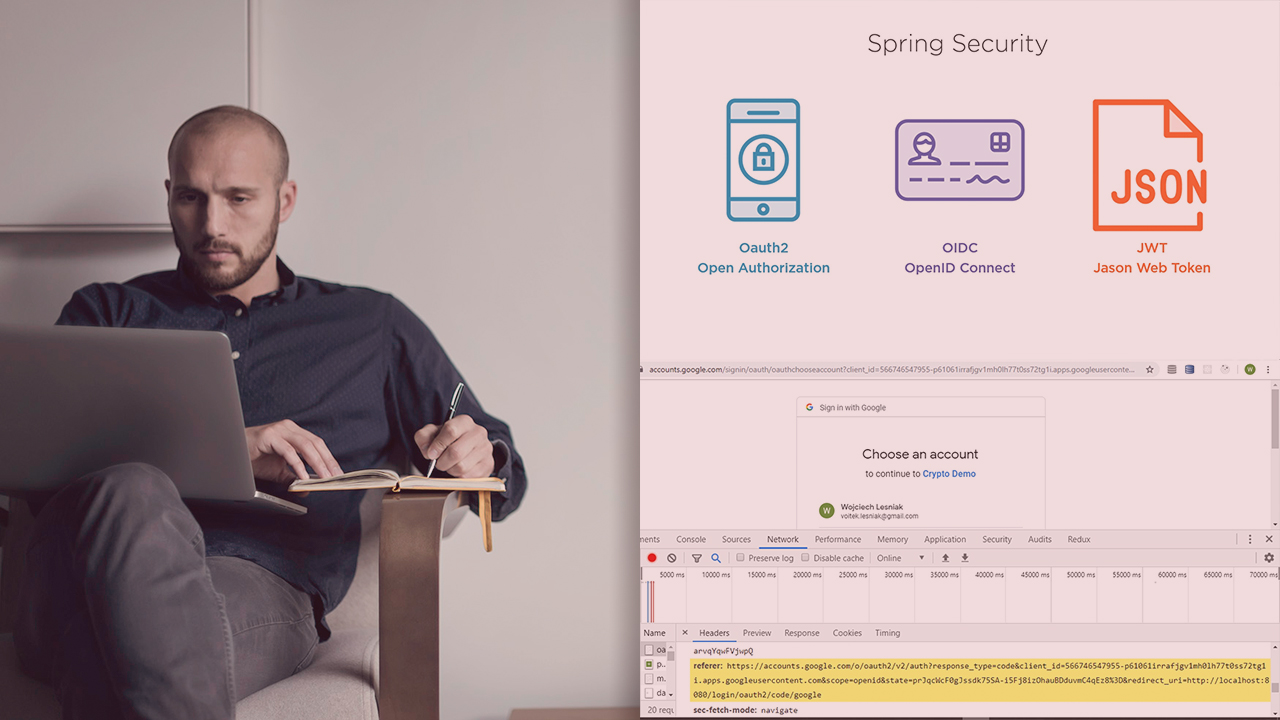
Securing your application with OAuth2, OIDC and JWT in your application can seem like a daunting task. In this course you will learn how to leverage Spring Security with Spring Boot to quickly and effectively do all the heavy lifting for you.
- Course
Effective OAuth2 with Spring Security 5 and Spring Boot
Securing your application with OAuth2, OIDC and JWT in your application can seem like a daunting task. In this course you will learn how to leverage Spring Security with Spring Boot to quickly and effectively do all the heavy lifting for you.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Core Tech
What you'll learn
Securing your application with OAuth2, OIDC and JWT doesn't have to be difficult. In this course, Effective OAuth2 with Spring Security 5 and Spring Boot, you will gain the ability to effectively leverage the framework to quickly and effectively do the heavy lifting for you. First, you will learn the essentials of OAuth2, OpenID Connect and JSON Web Token standards so you can correctly leverage Spring Security to add social sing-in to you existing application. Next, you will discover options on how to implement an Authorization Server so that you can completely decouple user authentication from you application code. Finally, you will explore more advanced topics on how to tailor the framework to your unique security requirements and the various patterns you can leverage to secure distributed systems such as microservices. When you are finished with this course, you will have the skills and knowledge of OAuth2 support in Spring Security needed to leverage OAuth2, OIDC and JWT in modern distributed applications.
Effective OAuth2 with Spring Security 5 and Spring Boot
-
Introduction | 1m 43s
-
Version Check | 15s
-
The Challenges with Authentication/Authorization in Modern Applications | 4m 3s
-
Why Tokens? | 4m 57s
-
Introducing JSON Web Tokens (JWT) | 2m 43s
-
A Journey into OAuth2 | 1m 53s
-
Autherization Code Grant | 4m 12s
-
OAuth2 Is Not Authentication | 1m 19s
-
Why We Need OpenID Connect | 3m 15s
-
What Makes OIDC Great for Authentication? | 5m 55s
-
OIDC Authorization Code Grant Flow | 1m 50s
-
Spring Security 5 the New Direction | 1m 34s

