- Course
Remote Code Execution in Erlang/OTP CVE-2025-32433: What You Should Know
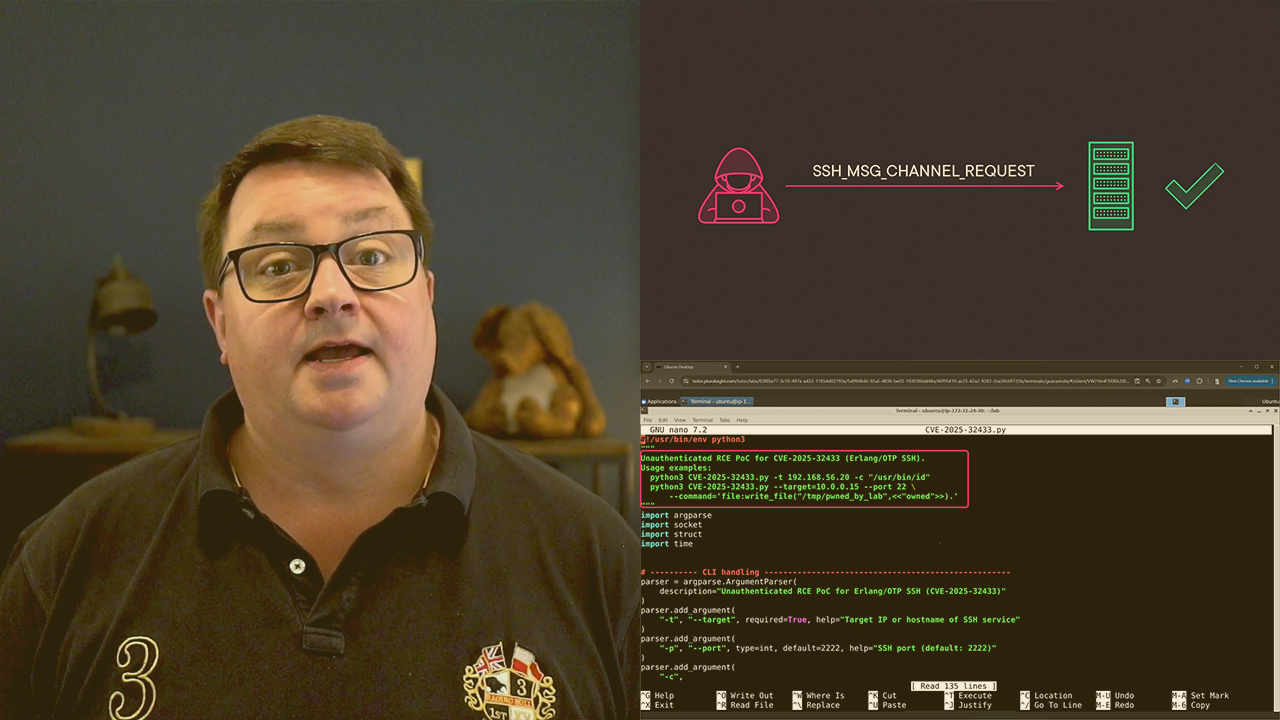
CVE‑2025‑32433 is a critical, CVSS 10.0 vulnerability that lets an unauthenticated attacker run arbitrary code through Erlang/OTP’s built‑in SSH server.
- Course
Remote Code Execution in Erlang/OTP CVE-2025-32433: What You Should Know
CVE‑2025‑32433 is a critical, CVSS 10.0 vulnerability that lets an unauthenticated attacker run arbitrary code through Erlang/OTP’s built‑in SSH server.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
Erlang is a functional language engineered for always‑on, soft real‑time services such as telecom switches, trading engines, and chat platforms. Its Open Telecom Platform (OTP) adds message‑passing middleware, hot‑code upgrades, a distributed database and a full tool‑chain.
On 16 April 2025, it was disclosed that a flaw in the built‑in Erlang/OTP SSH server let an unauthenticated attacker slip a crafted protocol message past the handshake and run arbitrary code. The issue carries a maximum CVSS v3 score of 10.0 and affects all deployments older than OTP‑27.3.3, 26.2.5.11 and 25.3.2.20. Major vendors, including Cisco, have acknowledged exposure, and public scans appeared within days of disclosure.
This course moves quickly from architecture fundamentals to hands‑on defense. You will see the exploit executed in a safe lab, learn how to spot vulnerable nodes in production, apply official patches or temporary mitigations, and adopt secure‑coding habits that harden future Erlang/OTP services. By the end, you’ll be ready to keep high‑availability systems online, even when the next zero‑day drops.

