- Course
Reverse Engineering Malware with Ghidra
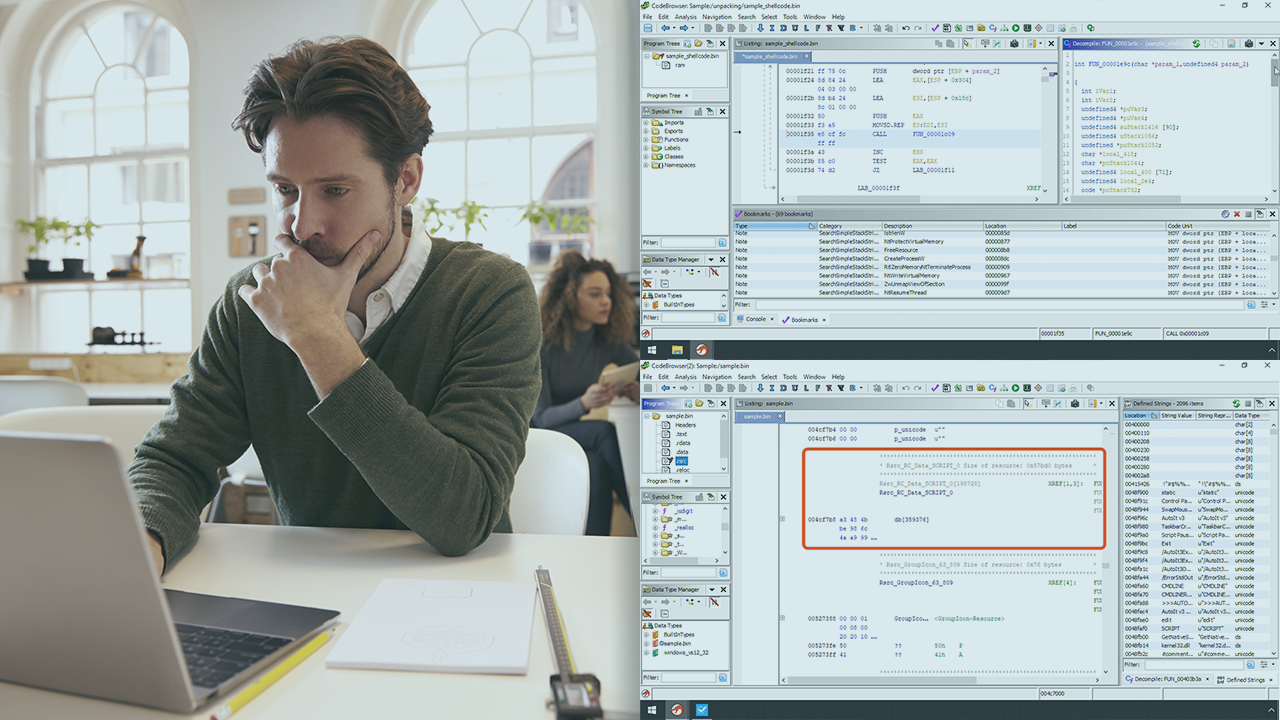
Reverse engineering is a key skill for malware analysts and security researchers. In this course, you will learn how to utilize the NSA's Ghidra reverse engineering tool to take your reversing skills to the next level.
- Course
Reverse Engineering Malware with Ghidra
Reverse engineering is a key skill for malware analysts and security researchers. In this course, you will learn how to utilize the NSA's Ghidra reverse engineering tool to take your reversing skills to the next level.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
The reverse engineering landscape has changed with the introduction of the National Security Agencies’ (NSA) software reverse engineering framework Ghidra, which is a fully-featured, open-source framework for performing reverse engineering of binary code. In this course, Reverse Engineering Malware with Ghidra, you will gain the ability to utilize Ghidra to perform reverse engineering of malware. First, you will learn how to install Ghidra and setup your first project. Next, you will discover how to maximize the user interface to aid in your reverse engineering goals. Finally, you will get hands-on with the decompiler and scripting engine by unpacking a modern trojan. When you're finished with this course, you will have the skills and knowledge of Ghidra needed to reverse engineer malware.

