- Course
Scanning for Vulnerabilities with Nmap 7 Scripting Engine (NSE)
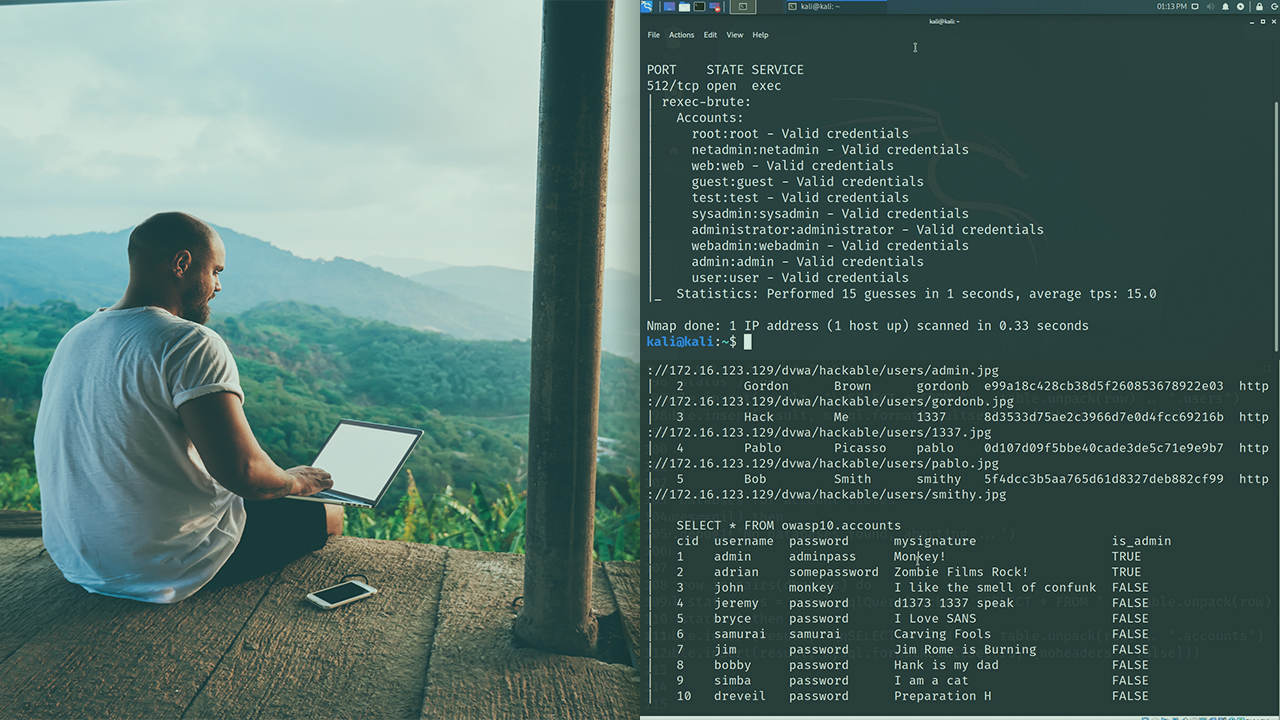
This course will teach you how to use the built-in and custom scripts of Nmap Scripting Engine (NSE) to detect vulnerabilities.
- Course
Scanning for Vulnerabilities with Nmap 7 Scripting Engine (NSE)
This course will teach you how to use the built-in and custom scripts of Nmap Scripting Engine (NSE) to detect vulnerabilities.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
Testing network security controls and discovering vulnerabilities are important parts of an organization's security plan. In this course, Scanning for Vulnerabilities with Nmap 7 Scripting Engine (NSE), you’ll learn to leverage the NSE and write custom scripts for Nmap. First, you’ll explore built-in NSE scripts. Next, you’ll discover network vulnerabilities of different types. Finally, you’ll learn how to write custom NSE scripts to detect and exploit vulnerabilties. When you’re finished with this course, you’ll have the skills and knowledge of the Nmap Scripting Engine needed to detect network vulnerabilities and write custom scripts.

