- Course
Secure Coding: Preventing Sensitive Data Exposure
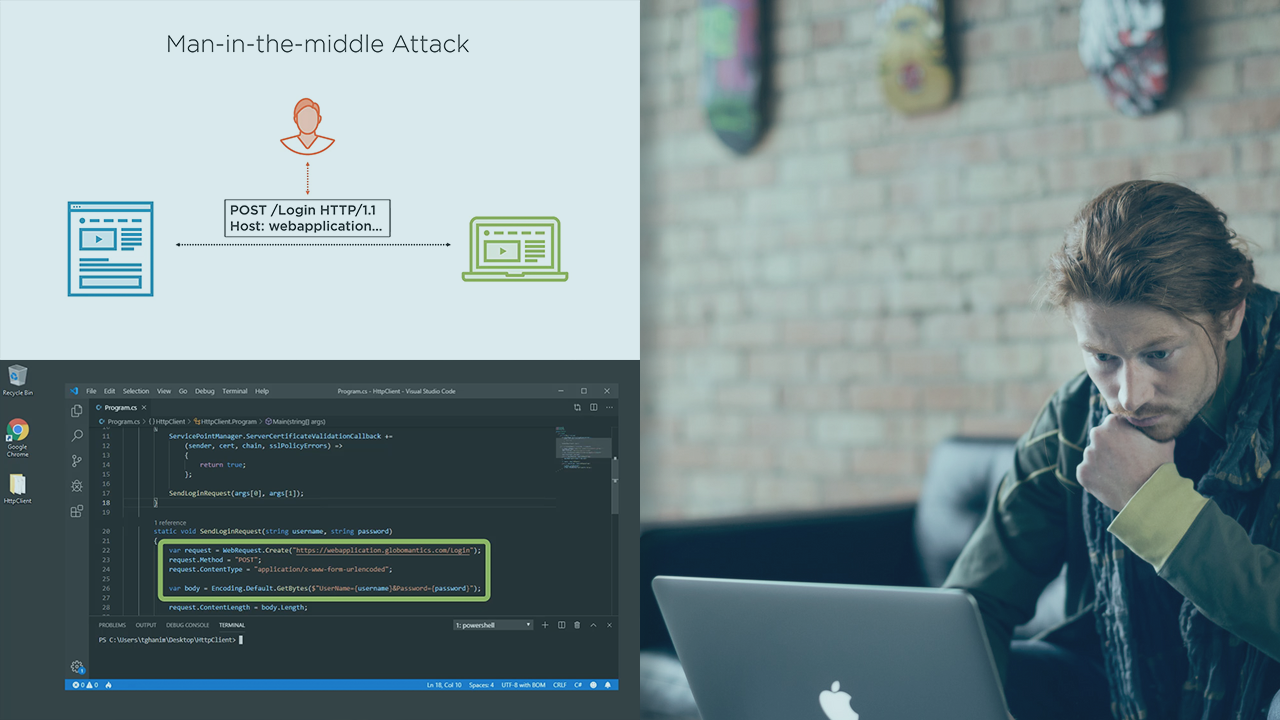
In this course, you will look from an attack-driven perspective at several OWASP recommendations for preventing sensitive data exposure when developing a web application.
- Course
Secure Coding: Preventing Sensitive Data Exposure
In this course, you will look from an attack-driven perspective at several OWASP recommendations for preventing sensitive data exposure when developing a web application.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Core Tech
What you'll learn
Would you like the ability to recognize what is needed to make a web application properly manage sensitive data and prevent it from unintended exposure? This course, Secure Coding: Preventing Sensitive Data Exposure, will show you the knowledge that is based on the recommendations set by the Open Web Application Security Project (or OWASP in short). First, you will learn how to think of sensitive data and what constitutes sensitive data. Next, you will discover TLS; the protocol to protect sensitive data transmitted between a web browser and web application and the different facilities it provides to enable this protection. Finally, you will explore how to properly manage user passwords stored in a database. When you’re finished with this course, you will have the knowledge of preventing sensitive data exposure needed to effectively and efficiently apply them in your own Web applications.

