- Course
Authentication Bypass in Security Edge Appliances: What You Should Know
Discover the key information you need to know about authentication bypass using a recently discovered vulnerability in a next-gen firewall as a case study.
- Course
Authentication Bypass in Security Edge Appliances: What You Should Know
Discover the key information you need to know about authentication bypass using a recently discovered vulnerability in a next-gen firewall as a case study.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
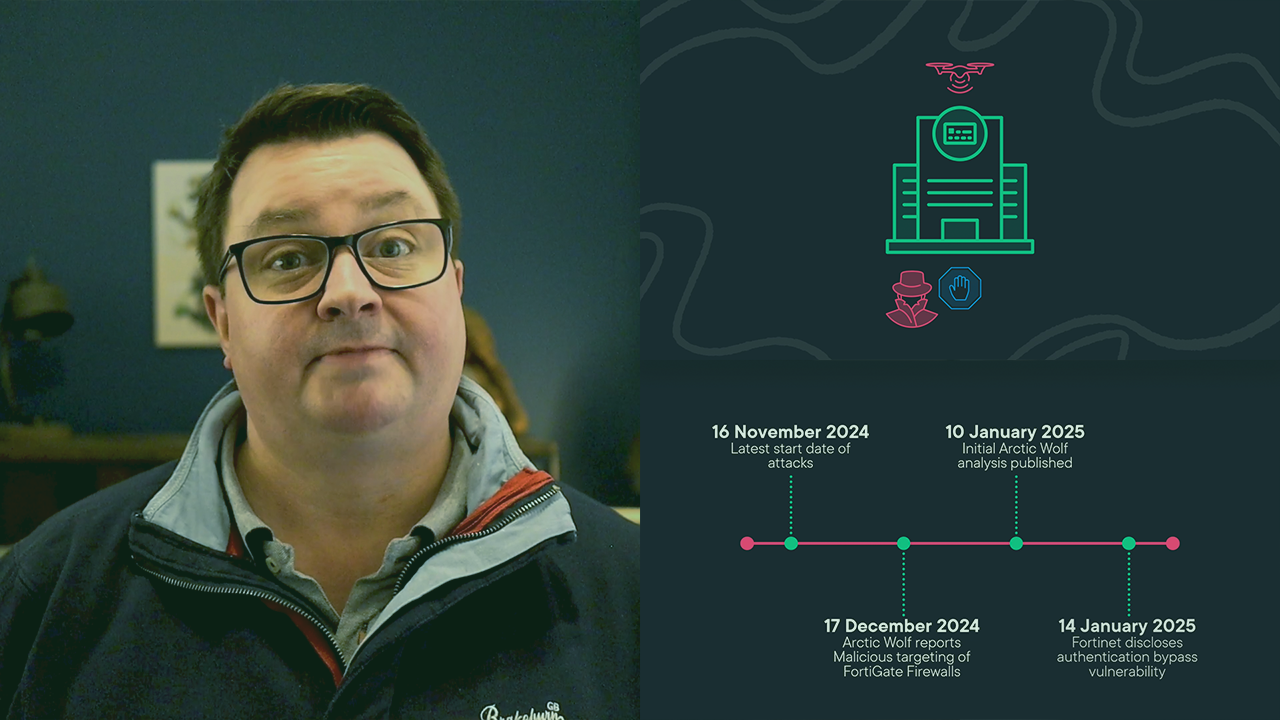
In this episode of What You Should Know we look at authentication bypass in security edge appliances. Attackers are increasingly targeting edge devices to gain initial access to victim environments, with 2024 seeing the largest ever year-on-year rise in incidents that resulted in an impact. Using CVE-2024-55591, an authentication bypass vulnerability affecting FortiOS and FortiProxy as a case study, we’ll explore analysis by Arctic wolf that monitored threat actors who used this weakness to gain super-admin access to Fortinet’s next-generation firewall. With this course, you’ll understand what this vulnerability means to you, what indicators of compromise to look for in your environment, and the steps you need to take to mitigate your organization’s exposure.

