- Course
Deploy Azure Kubernetes Service (AKS)
Kubernetes is the industry standard for deploying, scaling, and managing containerized applications. This course will teach you how to deploy Azure Kubernetes Service (AKS) and configure authentication and authorization for the cluster.
Deploy Azure Kubernetes Service (AKS)
- Course
Deploy Azure Kubernetes Service (AKS)
Kubernetes is the industry standard for deploying, scaling, and managing containerized applications. This course will teach you how to deploy Azure Kubernetes Service (AKS) and configure authentication and authorization for the cluster.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Cloud
What you'll learn
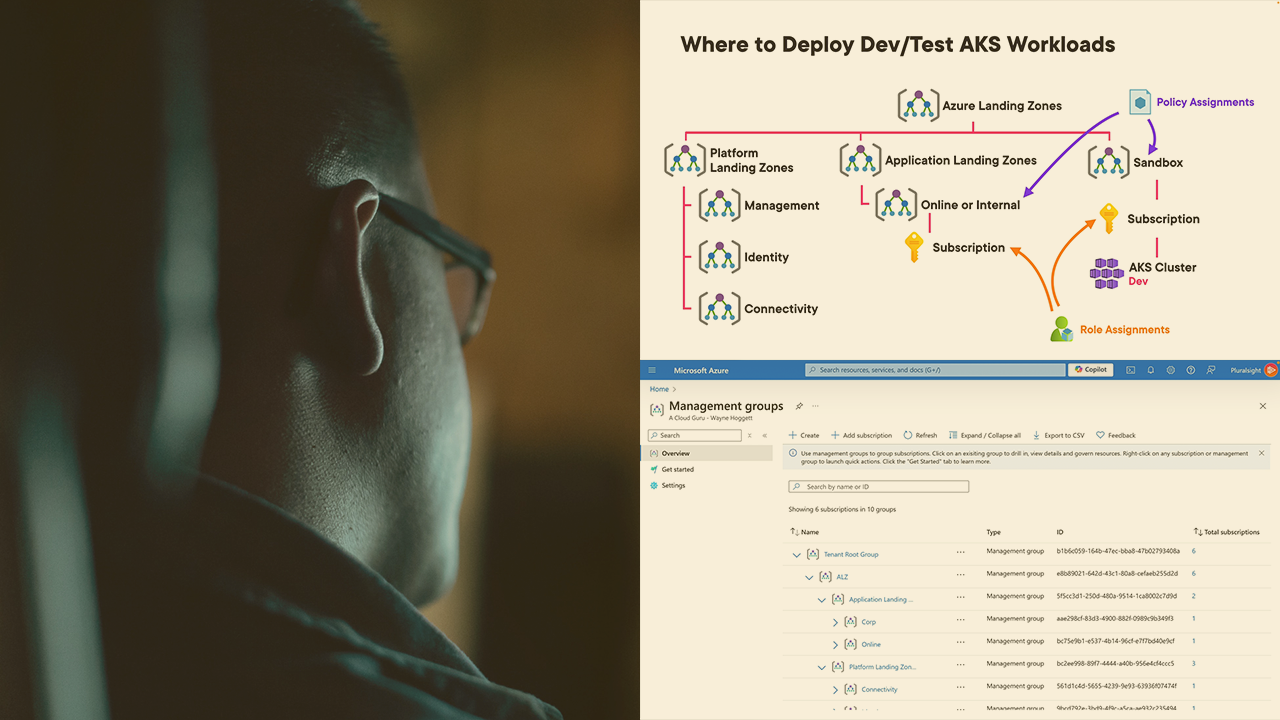
As organizations adopt cloud-native applications and services, the need for effective management and orchestration of containerized workloads becomes crucial. Azure Kubernetes Service (AKS) eases many of the challenges of managing a Kubernetes cluster by providing Kubernetes as a managed service. You can deploy development and test clusters and production clusters using a variety of deployment methods and configuration options. In this course, Deploy Azure Kubernetes Service (AKS), you'll learn the most common deployment methods and the recommended configuration options related to authentication and authorization for production-ready clusters. First you’ll discover how to deploy clusters for development and test environments. Next, you’ll explore how to deploy production-ready clusters using accelerators and AKS automatic. Then, you’ll access the cluster API. You’ll also learn how to configure namespaces, authentication using Microsoft Entra, authorization using Kubernetes roles, and Azure RBAC. When you’re finished with this course, you will have an understanding of how to deploy both dev/test and production-ready AKS clusters, and how to configure authentication and authorization in-line with production best practices. This will provide a foundation for you to move forward to continue to configure your clusters and deploy containerized applications to your cluster.

