- Course
Exploitation and Post-exploitation with Metasploit
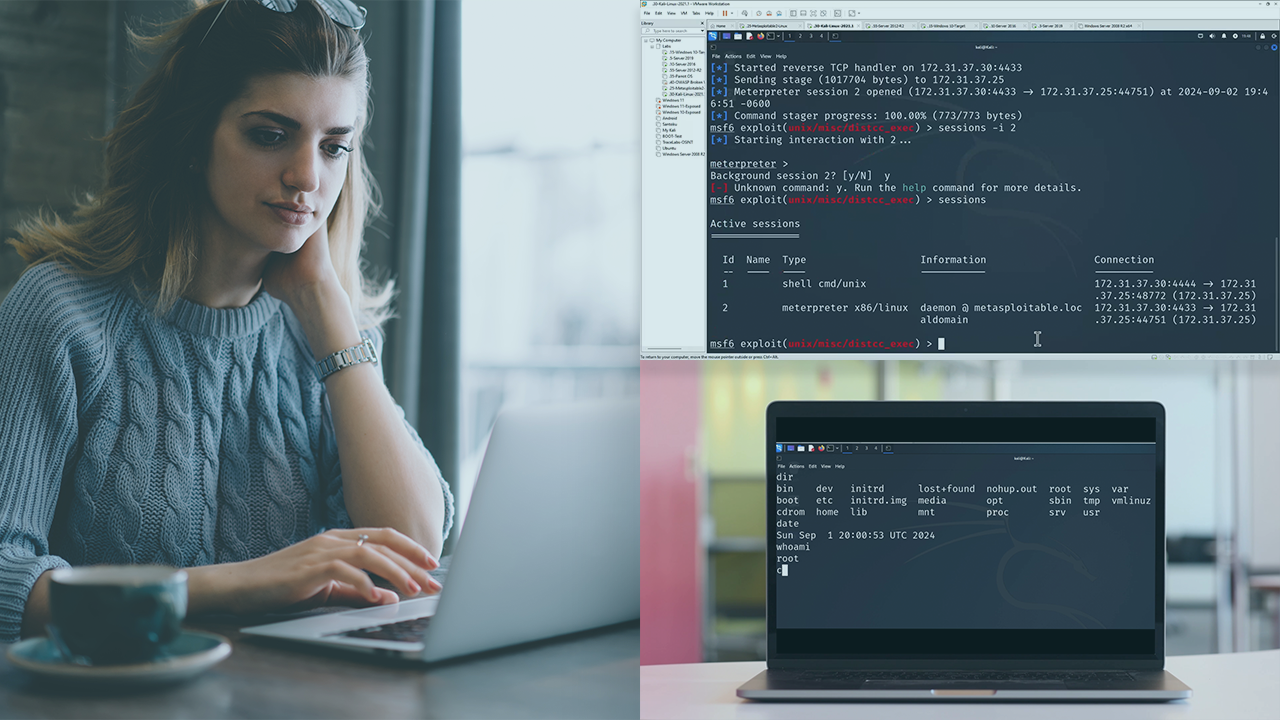
This course teaches you how to exploit and maintain access to vulnerable systems using Metasploit. You'll gain practical skills in exploiting known vulnerabilities and conducting post-exploitation with Meterpreter.
- Course
Exploitation and Post-exploitation with Metasploit
This course teaches you how to exploit and maintain access to vulnerable systems using Metasploit. You'll gain practical skills in exploiting known vulnerabilities and conducting post-exploitation with Meterpreter.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
In today's crazy world of threats, understanding how to exploit and leverage vulnerabilities is crucial for effective penetration testing. In this course, Exploitation and Post-exploitation with Metasploit, you'll learn how to exploit known vulnerabilities using the Metasploit Framework and perform advanced post-exploitation tasks. First, you'll explore how to use Metasploit’s vulnerability database to identify and exploit weaknesses in target systems. Next, you’ll discover how to maintain access and control over compromised systems using Meterpreter, including privilege escalation and lateral movement. Finally, you'll learn how to exfiltrate sensitive data while maintaining stealth and persistence on the target. By the end of this course, you'll have the practical skills and knowledge needed to carry out advanced exploitation and post-exploitation techniques using Metasploit.

