- Course
Information and Cyber Security Literacy: Security Operations
A thorough understanding of the roles and responsibilities within a security operations center is vital to safeguarding your company’s assets.
- Course
Information and Cyber Security Literacy: Security Operations
A thorough understanding of the roles and responsibilities within a security operations center is vital to safeguarding your company’s assets.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
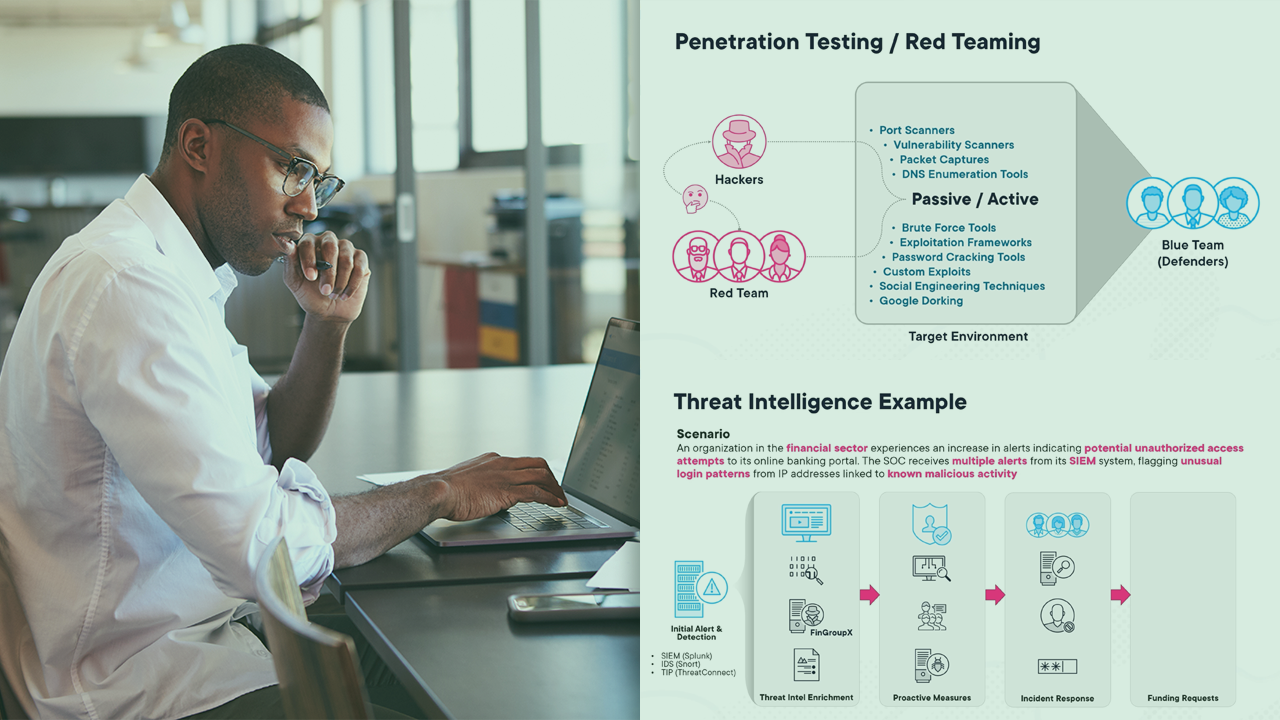
In today's interconnected world, the threat landscape looms large, with cyberattacks becoming increasingly sophisticated and prevalent. Arm yourself against this pervasive threat in this course, Information and Cyber Security Literacy: Security Operations. First, you’ll delve into the pivotal roles within a Security Operations Center (SOC). Next, you’ll dig deeper into penetration testing and discuss the roles, responsibilities, and capabilities that exist to uncover vulnerabilities before adversaries do. Lastly, you’ll discuss the benefits and strategic insights gained by threat intelligence analysis to proactively defend against emerging threats. At the end of this course, you’ll be equipped with a deeper understanding of the skills and capabilities necessary to navigate the complex terrain of cybersecurity and safeguard digital assets with confidence.
Information and Cyber Security Literacy: Security Operations
-
Module Intro | 1m 44s
-
Security Operations Center Main Roles | 2m 52s
-
Security Analysts: Roles, Responsibilities and Common Tools | 3m 52s
-
Incident Responders: Types and Responsibilities | 2m 42s
-
Threat Hunters: Roles, Responsibilities, and Common Tools | 2m 14s
-
SOC: Interconnected Roles and Responsibilities | 1m 42s
-
Threat Types: Internal and External | 3m 23s
-
Module Intro | 1m 51s
-
Specific Types of Threats | 2m 7s
-
Gathering and Correlating Information | 1m 19s
-
Strategic, Tactical, and Operational Intelligence | 1m 52s
-
Common Tools, SIEM Systems, and How Intelligence Adds Value | 2m 21s
-
Security Operations Maturity Levels | 2m 31s
-
Categories of Threat Intelligence in Industry Verticals | 1m 22s
-
SOC: Interconnected Roles and Responsibilities | 2m
-
Demo: Enriching Alerts with Threat Intelligence | 5m 29s

