- Course
Implementing and Managing Microsoft Defender for Endpoint
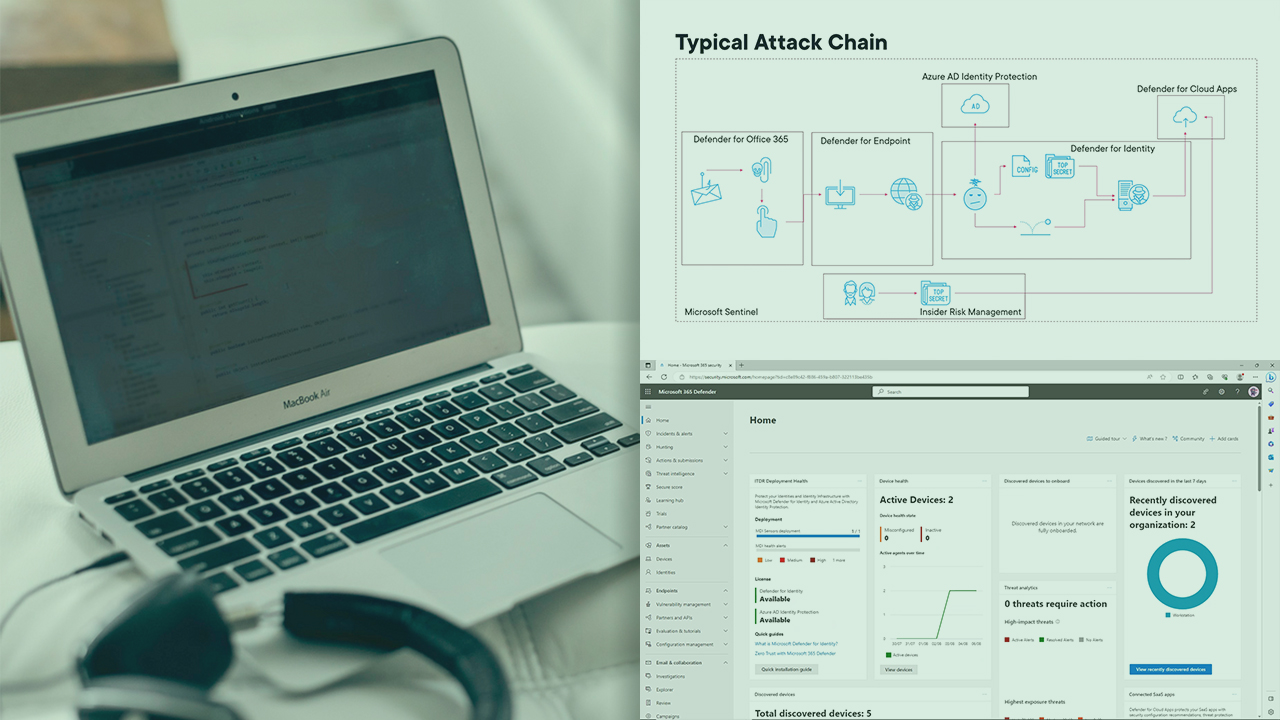
This course will teach you to successfully deploy Microsoft Defender for Endpoint, perform advanced configuration, and fully manage the solution.
- Course
Implementing and Managing Microsoft Defender for Endpoint
This course will teach you to successfully deploy Microsoft Defender for Endpoint, perform advanced configuration, and fully manage the solution.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Core Tech
What you'll learn
In your organization today, you have a diverse set of endpoints that are being used. These entail different operating systems on PCs, servers, and mobile devices. Cybersecurity threats are rampant and span across all of these types of devices, and since your endpoints are keys into your organization network, it's imperative that these are protected. In this course, Implementing and Managing Microsoft Defender for Endpoint, you will learn to successfully plan, deploy, and manage Microsoft Defender for Endpoint. First, you will explore the various ways Microsoft Defender for Endpoint can be deployed and the advanced configuration options. Next, you will discover how to enforce enhanced protections using attack surface reduction rules. Finally, you will gain an overview on the types of threats that Microsoft Defender for Endpoint is able to mitigate against. When you are finished with this course, you will have the skills and knowledge of implementing and managing Microsoft Defender for Endpoint needed to fully deploy and manage it successfully.

