- Course
Implement User-ID on Palo Alto Firewalls
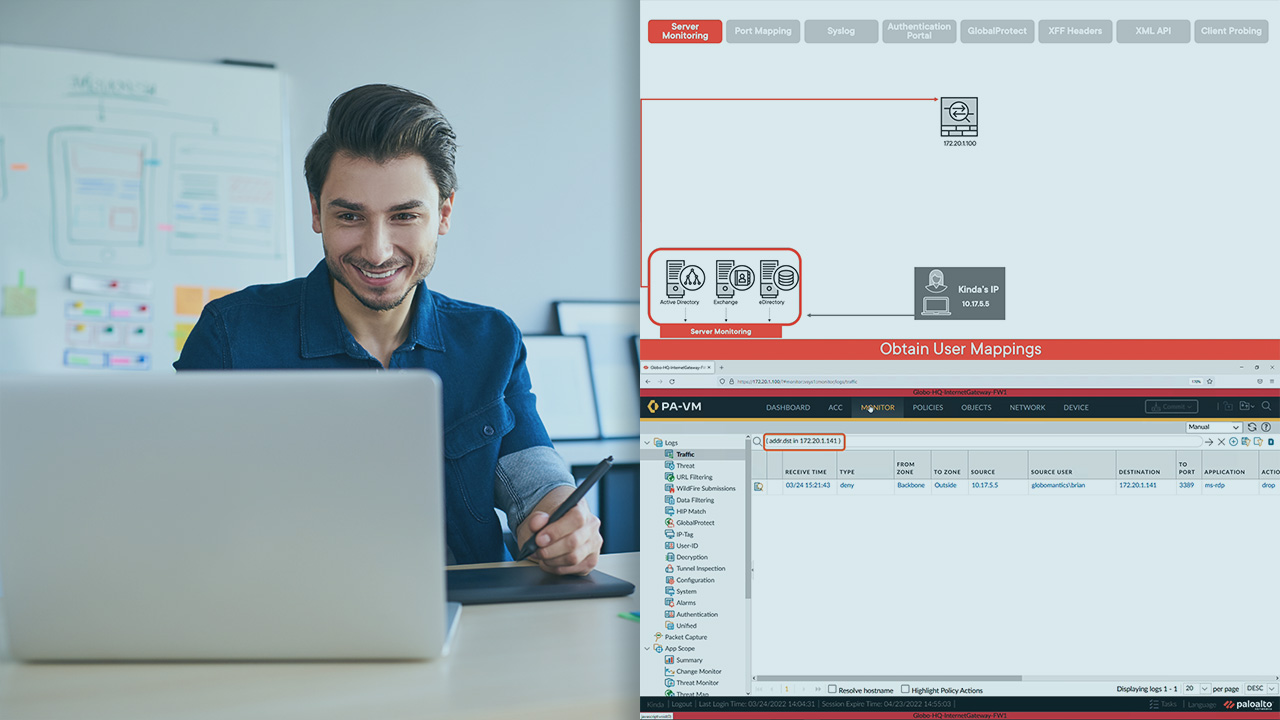
Leveraging user information on your network allows you to create granular policies. This course will teach you how to utilize User-ID to gain information on the users on your network and create security rules specific to them.
- Course
Implement User-ID on Palo Alto Firewalls
Leveraging user information on your network allows you to create granular policies. This course will teach you how to utilize User-ID to gain information on the users on your network and create security rules specific to them.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Core Tech
What you'll learn
Without identifying the users in your network, a malicious actor could easily switch IP addresses to gain unauthorized access. In this course, Implement User-ID on Palo Alto Firewalls, you’ll learn to leverage User-ID to create granular rules that are user specific. First, you’ll explore how to configure User-ID to leverage Active Directory security groups in your security rules. Next, you’ll discover how to create dynamic groups if unauthorized traffic occurs, which can have remediation policies applied. Finally, you’ll learn how to identify users who are using devices that are not known by User-ID. When you’re finished with this course, you’ll have the skills and knowledge of User-ID needed to identify users and create granular policies specific to them.
Implement User-ID on Palo Alto Firewalls
-
Palo Alto Networks’ User-ID | 7m 54s
-
User-ID Requirements | 8m 31s
-
Demo: Create a Secure User-ID Service Account | 5m 44s
-
Demo: Configure User-ID Agent on an Active Directory Server | 10m 19s
-
Demo: Implement User-ID Components on a Palo Alto Firewall | 5m 10s
-
Demo: Implement User-ID Into Security Policies | 4m 38s
-
Demo: Verify User-ID is Working Properly | 5m 34s
-
Demo: Redistribute User-ID Mappings to Other Firewalls | 9m 54s

