- Course
Post-exploitation and Lateral Movements for CompTIA Pentest+
This course teaches you how to establish persistence, execute lateral movements, exfiltrate data, and perform cleanup operations, preparing you for the CompTIA PenTest+ exam.
- Course
Post-exploitation and Lateral Movements for CompTIA Pentest+
This course teaches you how to establish persistence, execute lateral movements, exfiltrate data, and perform cleanup operations, preparing you for the CompTIA PenTest+ exam.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
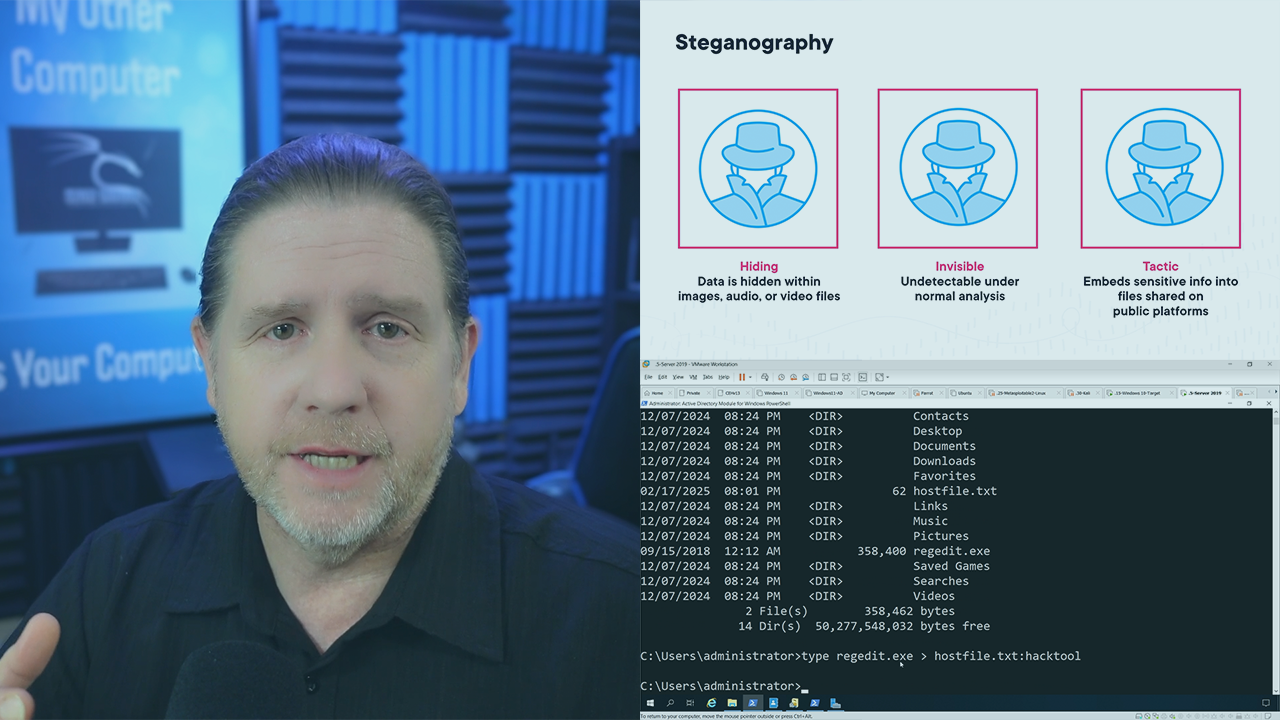
Post-exploitation techniques are critical for maintaining access, moving laterally, and extracting data in a controlled and ethical penetration testing engagement. In this course, Post-exploitation and Lateral Movements for CompTIA PenTest+, you’ll gain the skills required to effectively navigate compromised environments. First, you’ll learn how to establish and maintain persistence using scheduled tasks, command-and-control frameworks, and rootkits. Next, you’ll explore lateral movement techniques, such as pivoting, service enumeration, and credential dumping, using tools like Mimikatz and Impacket. Finally, you’ll cover staging and exfiltration methods, as well as cleanup and restoration activities to revert changes and preserve evidence. By the end of this course, you’ll have the knowledge to execute post-exploitation techniques responsibly and effectively, fully preparing you for the CompTIA PenTest+ certification exam.

