- Course
Volt Typhoon: T1003.003 Credential Dumping Emulation
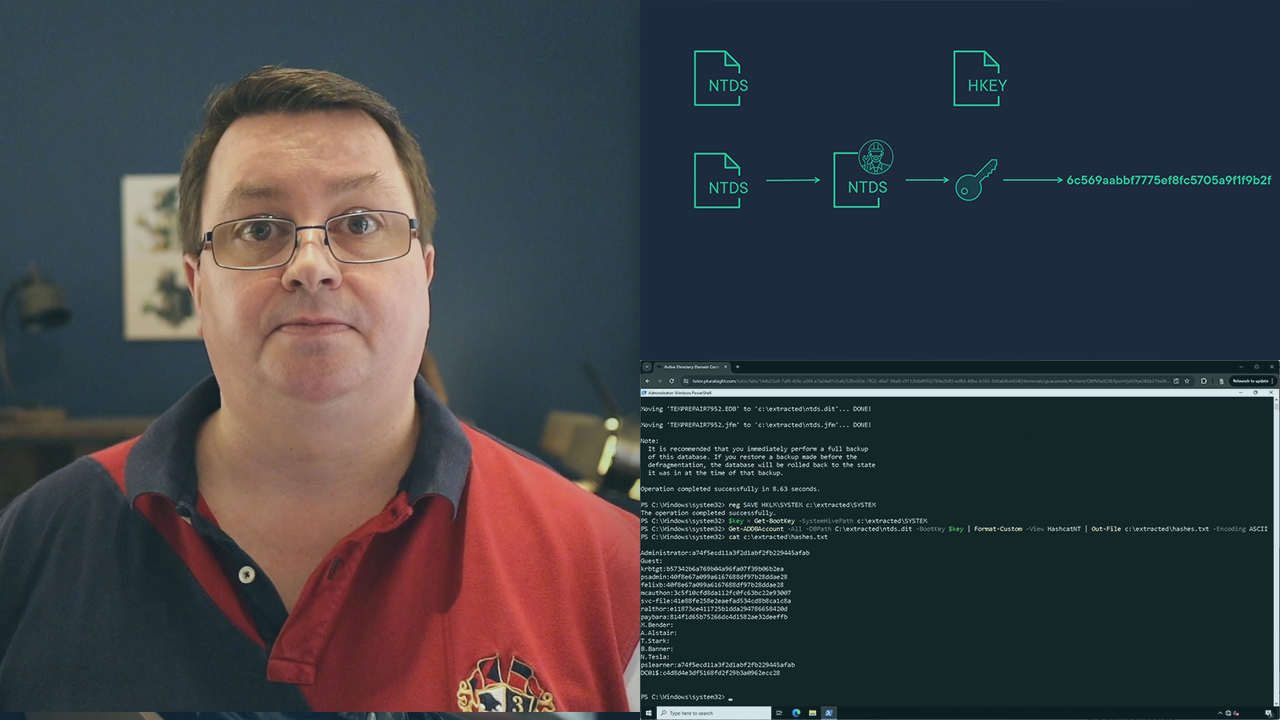
Explore how Volt Typhoon created a copy of the Active Directory domain database in a critical infrastructure network in order to steal credential information.
- Course
Volt Typhoon: T1003.003 Credential Dumping Emulation
Explore how Volt Typhoon created a copy of the Active Directory domain database in a critical infrastructure network in order to steal credential information.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
Adversaries often seek to extract user credentials, typically in the form of hashes or plaintext passwords, from operating systems and software. These credentials can then be used to facilitate lateral movement within a network and gain access to sensitive information. Volt Typhoon used a number of techniques to obtain credentials, including extracting them from process memory and stealing Active Directory databases (NTDS). In this course, Volt Typhoon: T1003.003 Credential Dumping Emulation, you’ll focus on how Volt Typhoon created a volume shadow copy and extracted the bootkey from the system registry hive to extract password hashes from NTDS.

