- Course
Windows Buffer Overflow Walkthrough
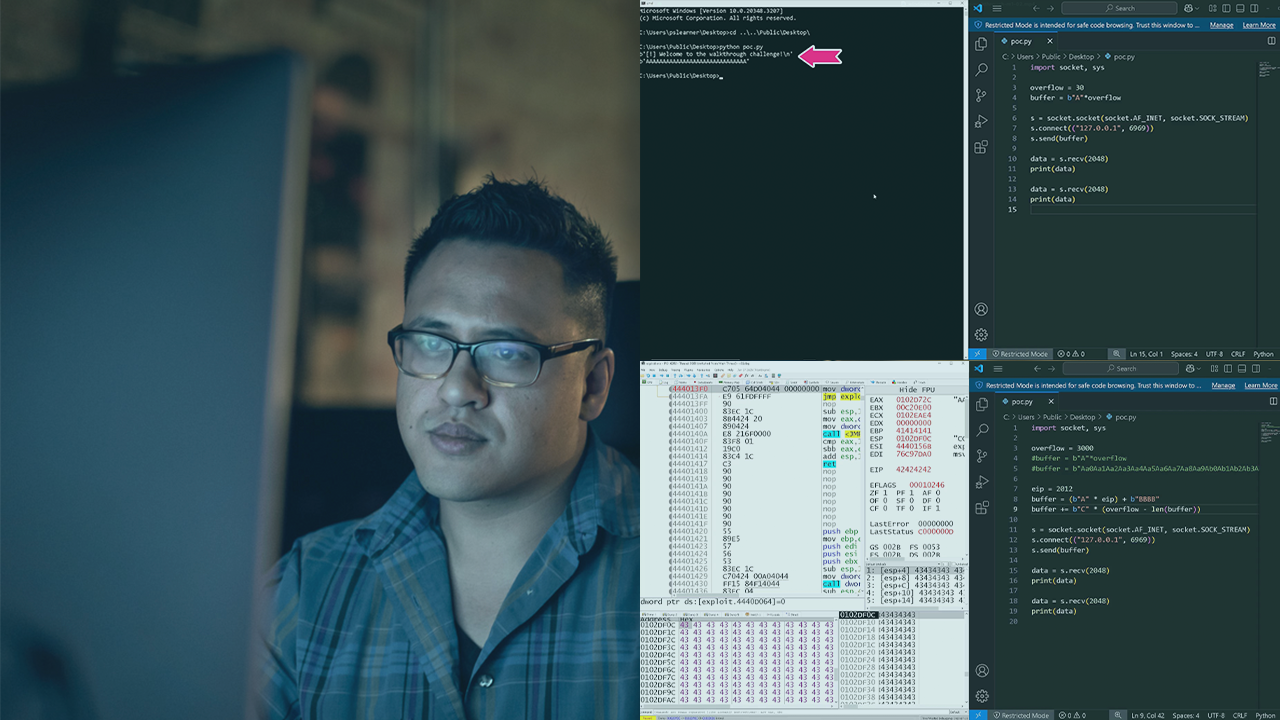
Gain hands-on experience identifying and exploiting x86 stack-based buffer overflow vulnerabilities, and develop a solid understanding of how this class of vulnerabilities can be exploited.
- Course
Windows Buffer Overflow Walkthrough
Gain hands-on experience identifying and exploiting x86 stack-based buffer overflow vulnerabilities, and develop a solid understanding of how this class of vulnerabilities can be exploited.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
Understanding how buffer overflows work is a foundational skill for anyone interested in software exploitation and vulnerability research. In this course, Windows Buffer Overflow Walkthrough, you’ll learn to identify, exploit, and gain control over a vulnerable application. First, you’ll explore how a stack-based buffer overflow occurs in an x86 process. Next, you’ll discover how to interface with and fuzz the vulnerable application while handling exceptions in a debugger. Finally, you’ll learn how to control the instruction pointer, generate shellcode, and execute it via the vulnerable application function. When you’re finished with this course, you’ll have the skills and knowledge for exploiting simple x86 stack-based buffer overflows in vulnerable programs. To follow along with the author on Pluralsight to solve the practical exercises demonstrated in the walkthrough, you can complete the Windows Buffer Overflow Exploitation lab.

