- Course
Fundamentals of OT Protocols
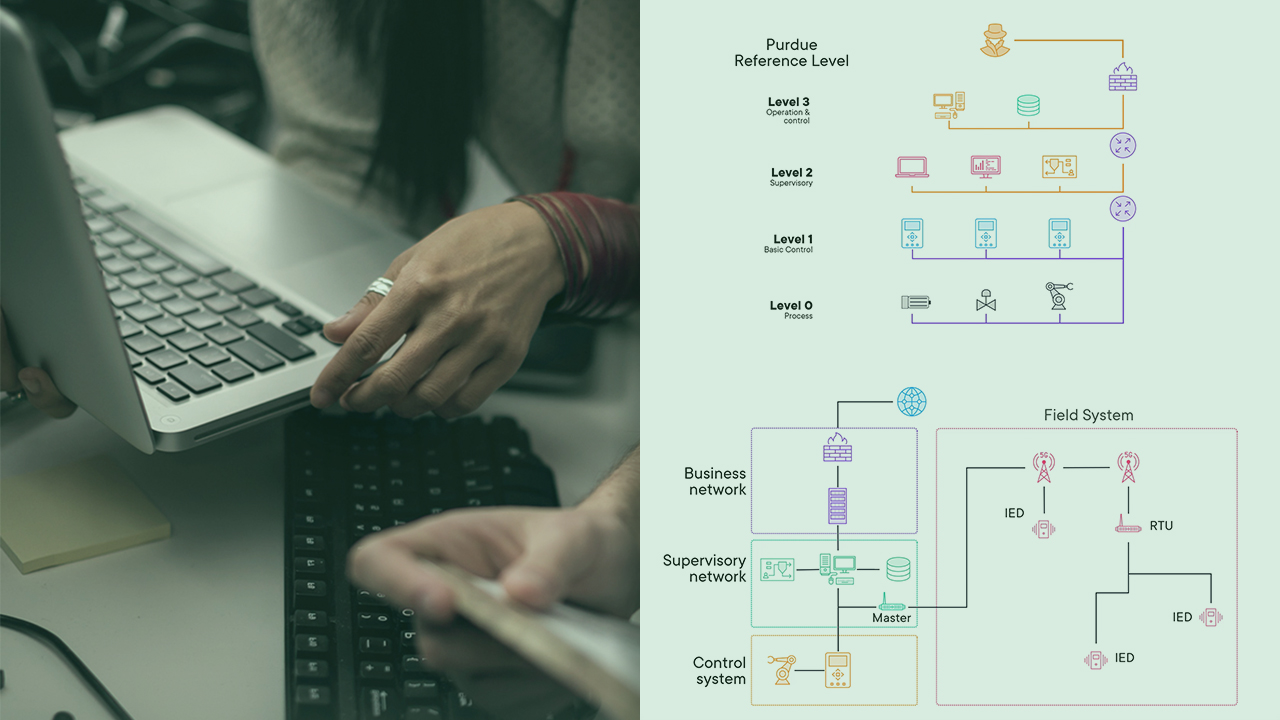
In this course you’ll explore OT protocols to identify weaknesses and vulnerabilities that could be exploited to cause real-world physical impacts, and identify effective controls that will help to reduce the likelihood of a successful attack.
- Course
Fundamentals of OT Protocols
In this course you’ll explore OT protocols to identify weaknesses and vulnerabilities that could be exploited to cause real-world physical impacts, and identify effective controls that will help to reduce the likelihood of a successful attack.
Get started today
Access this course and other top-rated tech content with one of our business plans.
Try this course for free
Access this course and other top-rated tech content with one of our individual plans.
This course is included in the libraries shown below:
- Security
What you'll learn
It is pivotal to have a foundational understanding of Operational Technology (OT) protocols, their inherent weaknesses and vulnerabilities, and the challenges of securing them. In this course, Fundamentals of OT Protocols, you’ll explore networking protocols used in industrial processes and other critical infrastructure to understand how they work and how they have been developed to meet high reliability and efficiency needs. First, you’ll explore three of the most common OT protocols: Modbus, DNP3 and Ethernet/IP, and learn how to interpret packet captures of different protocol behaviors. Next, you’ll discover weaknesses and vulnerabilities in OT protocols and learn about the techniques that attackers use to exploit them. Finally, you’ll identify security recommendations based on secure architecture, network detection and perimeter security to help mitigate the threat of attacks against OT protocols. When you’re finished with this course, you’ll have the skills and knowledge to apply your understanding to other OT protocols and to implement practical security controls to reduce exposure to threats against operational technology.

